Security is of great concern today.Here are the steps Enabling SSL in Oracle Apps R12
Introduction:
- The data between web browser and web server travels unencrypted in R12 application So the password and other information can be tracked by sniffer. They can get your Username/Password or any sensitive data. This become critical when you have Internet access to Oracle Applications
- With SSL implementation, the data travels in the encrypted forms and Only web browser and web server can decrypt it.The implementation requires the SSL certificate and configuration in the R12 environment as per the configuration
What is SSL?
SSL and TLS are the cryptographic protocol that ensures privacy between communicating applications and their users on the Internet
What are SSL certificates
SSL uses 2 types of Certificates:
User certificates:
These are Certificates issued to servers or users to prove their identity in a public key/private key exchange.
Trusted certificates:
These are Certificates representing entities that you trust – such as certificate authorities that sign the user certificates they issue.
Secure Sockets Layer (SSL)
SSL is a technology that defines the essential functions of mutual authentication, data encryption, and data integrity for secure transactions. Exchange of data between the client and server in such secure transactions is said to use the Secure Sockets Layer (SSL).
Transport Layer Security (TLS)
Transport Layer Security is a cryptographic protocol that ensures privacy between communicating applications and their users on the Internet. While SSL is supported with all versions of the Oracle Application Server, TLS requires a minimum of Application Server 10.1.2.0.Oracle Applications Release 12 supports the use of both SSL and TLS.
How SSL works
- The client sends a request to the server using HTTPS connection mode.
- The server presents its digital certificate to the client. This certificate contains the server’s identifying information like server name, Organization and server public key and digital signature of the CA private key
- The client (web browser) has the public keys of the all the CA. It decrypts the digital certificate private key This verification proves that the sender had access to the private key, and therefore is likely to be the person associated with the public key. If the verification goes good, the server is authenticated as a trusted server.
- The client sends the server a list of the encryption levels, or ciphers, that it can use.
- The server receives the list and selects the strongest level of encryption that they have in common.
- The client encrypts a random number with the server’s public key and sends the result to the server (which only the server should be able to decrypt with its private key); both parties then using the random number to generate a unique session key for subsequent encryption and decryption of data during the session
So it is clear from the steps above, we will need a digital certificate for the webserver and We use Oracle wallet in 10.1.3 for the storing the certificate
Various Topology of SSL in Oracle Apps R12
The ssl Implementation will depend on the topology of the R12 implementation. I am here highlighting all the major one. This is both valid for R12.0 and R12.1 Implementation.
- A single webserver deployment.
This is pretty simple. We will need the digital certificate for the webserver. The steps are straight forward. The traffic between web browser and webserver will be encrypted
- Having a Load balancer which is serving to 2 or more webserver makes it little bit complicated
In this case, we could have following options
- End to end encryption of traffic
The entire traffic flow i.e. from browser to load balancer and from load balancer to web server is encrypted
There are two ways to do it
(a) Pass-through configuration: The load balance in this case does not decrypt/encrypt the message .it just passes through the traffic to the webserver
When configuring Ebusiness Suite with load balancing hardware you would of seen in numerous places the requirement to setup cookie based persistence. The problem we have here is that when SSL passthrough is in place cookie persistence will not function because the cookie is encrypted by Ebusiness Suite and the load balancer will not be able to read the cookie information needed to maintain persistency.Here is an extract from F5 documentation which explains this in more detail
Source:
http://devcentral.f5.com/Tutorials/TechTips/tabid/63/articleType/ArticleView/articleId/262/Persisting-SSL-Connections.aspx
For SSL Pass-through configurations, the persistence options are severely limited: Since LTM is not decrypting the conversation, only the non-SSL-encrypted information in the session is available for use as a session identifier. The primary pieces of persistent unencrypted information in an encrypted SSL flow are the source and destination IP addresses, and the SSL session ID itself, so only Source Address, Destination Address, or SSL persistence will work with SSL Pass-through configurations. When using Source Address persistence, this can create a situation where clients accessing the system from a proxy type device will all be stuck on the same application tier, causing an imbalance of traffic on the application tier. So using something more unique, like the SSL sessionid, is preferred.
We recommend setting SSL persistence as the primary persistence method, then set Source Address as a backup persistence method to stick new connections to the same server even if the SSL session ID changes mid-application session. It is also a best practice to then configure the application tier to minimize the number of SSL session re-negotiations, consult the appropriate application server administration guides for more information.As such, the recommendation is to use the SSL persistence profile as well as the Source Address profile.
However, you could simply run the Source Address profile on its own if the client IP is being passed to the load balancer.
Note: the persistence timeout assigned to the source address profile or the SSL profile should be increased to the Oracle recommended value of 12 hours.
(b) Decryption/encryption: The load balance in this case decrypt the traffic at the load balancer level and then again encrypt it and send it to web server which again decrypt it
2) SSL terminator: The traffic between web browser and load balancer is only encrypted. The Load balance acts as SSL terminator and terminate the SSL at the load balancer level and passes the unencrypted traffic to the webserver.It has following benefits.
Performance improvement: Offloading SSL Encryption and de-encryption to the load balancer significantly improves performance by reducing CPU load. As customers are now being issued SSL certificates with keys of 2048 bytes, the SSL processing CPU load on the application tier will be 5 times higher than using legacy 1024 byte SSL key
Steps to perform configuration on each topology is give below
A single webserver deployment SSL in Oracle Apps R12
Step 1
Set Your Environment
- Logon to the application tier as the OS user who owns the application tier files.
- Source your application tier environment file (APPS<sid_machine>.env) located in the APPL_TOP directory.
- Navigate to the $INST_TOP/ora/10.1.3 and source the <sid_machine>.env file to set your 10.1.3 ORACLE_HOME variables.
Note: When working with wallets and certificates you must use the 10.1.3 executables.
Important Note
If you are using clients (JRE 8, some modern browsers) or Oracle Database 12c, you must perform the following:
– Upgrade FMW 10.1.3 to 10.1.3.5
– Apply the October 2015 CPU (Patch 21845960).
Step 2
Create a wallet
- Navigate to the $INST_TOP/certs/Apache directory.
- Move the existing wallet files to a backup directory in case you wish to use them again in the future.
- Open the Wallet manager as a background process:
$ owm &
On the Oracle Wallet Manager Menu navigate to Wallet >New.
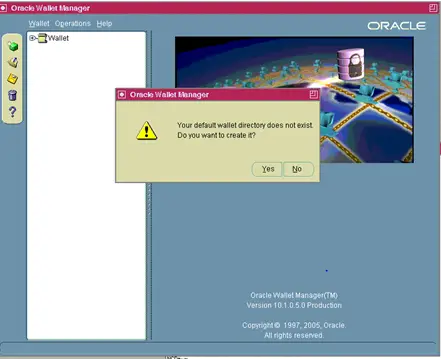
Answer NO to: Your default wallet directory doesn’t exist. Do you wish to create it now?
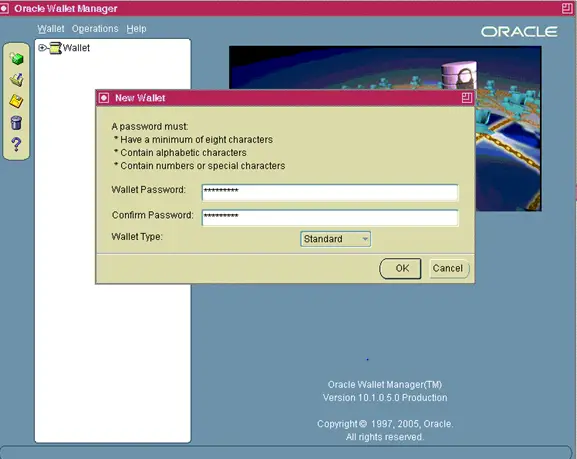
The new wallet screen will now prompt you to enter a password for your wallet
Enter the password and remember it
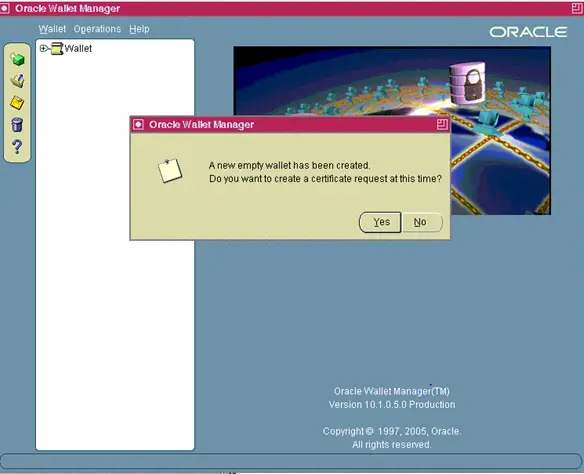
A new empty wallet has been created. Do you wish to create a certificate request at this time?
After clicking “Yes” in the Create Certificate Request Screen will pop up
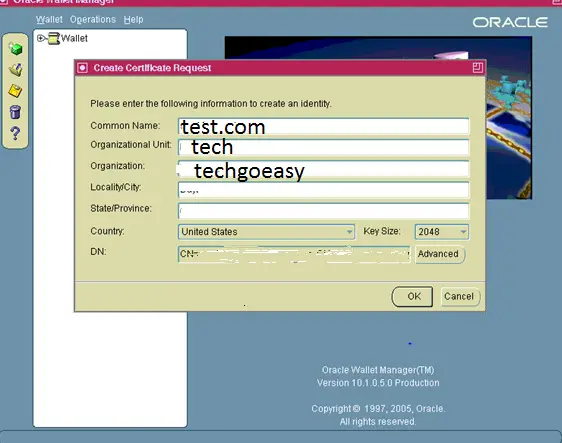
Fill in the appropriate values where:
| Common Name | It is the name of your server including the domain. |
| Organizational Unit: (optional) | The unit within your organization. |
| Organization | It is the name of your organization |
| Locality/City | It is your locality or city. |
| State/Province | is the full name of your State or Province do not abbreviate. |
Select your Country from the drop down list, and for the Key Size, select 2048 as a minimum. Click OK.
Note: Depending on your certificate provider, they may not accept the MD5 based certificate request (CSR) generated by the Oracle Wallet Manager (OWM). For example, VeriSign will now only accept SHA12048 bit based CSRs or higher. In such cases, you will need to convert the MD5 CSR to a suitable SHA1based CSR.
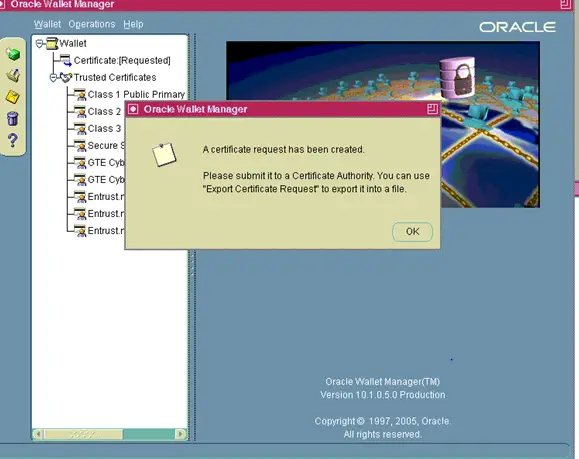
Click On certificate requested
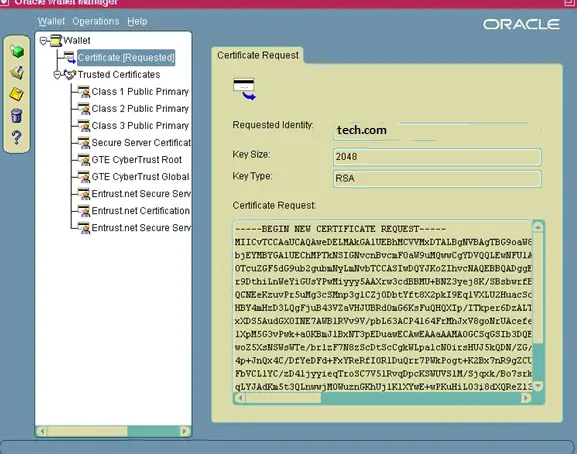
You will need to export the Certificate Request before you can submit it to a Certifying Authority.
- Click on Certificate [Requested] to Highlight it.
- From the menu click Operations >
Export Certificate Request
- Save the file as server.csr
- From the menu click Wallet and then click Save.
- On the Select Directory screen change the Directory to your fully qualified wallet directory.
- Click OK.
- From the menu click Wallet and check the Auto Login box.
Be sure to make this password something you will remember. You will need to use the password whenever you open the wallet with Oracle Wallet Manager or perform operations on the wallet using the Command Line Interface. With auto login enabled processes submitted by the OS user who created the wallet will not need to supply the password to access the wallet.
- Exit the Wallet Manager.
The wallet directory will now contain the following files:
cwallet.sso
ewallet.p12
server.csr
You may now submit server.csr to your Certifying Authority to request a Server Certificate
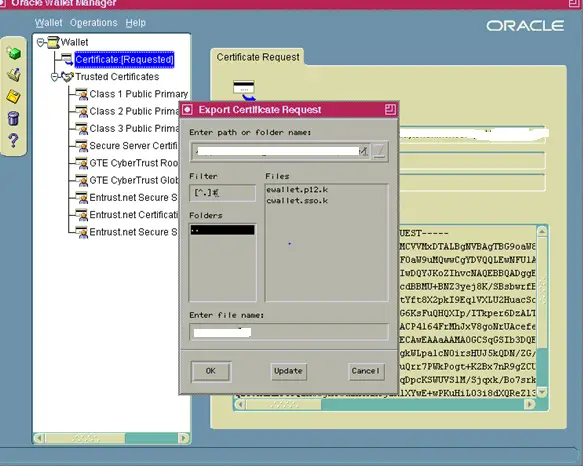
Step 5
Import your Server Certificate to the Wallet
After you receive your Server Certificate from your Certifying Authority you will need to import it into your wallet. Copy the certificate to tech.crt in the wallet directory on your server by one of the following methods:
- ftp the certificate (in binary mode)
- copy and paste the contents into server.crt
Follow these steps to import tech.crt into your wallet:
- Open the Wallet Manager as a background process:
$ owm &
- From the menu click Wallet then Open.
- Answer Yes when prompted:
Your default wallet directory does not exist.
Do you want to continue?
- On the Select Directory screen change the Directory to your fully qualified wallet directory and
click OK
- Enter your wallet password and click OK.
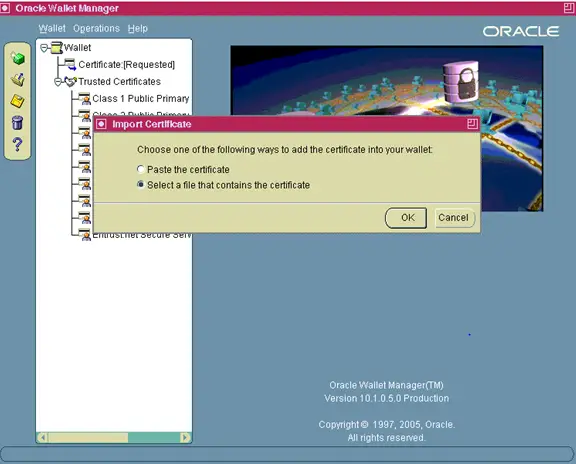
- On the Oracle Wallet Manager Menu navigate to Operations Import
User Certificate.
Server certificates are a type of user certificate. Since the Certifying Authority issued a certificate for the server, placing its distinguished name (DN) in the Subject field, the server is the certificate owner, thus the “user” for this user certificate.
- Click OK.
- Double Click on server.crt to import it.
- Save the wallet:
- On the Oracle Wallet Manager Menu click Wallet.
- Verify the Auto Login box is checked.
- Click Save
Note: If all trusted certificates that make up the chain of server.crt are not present in the wallet, then adding the certificate will fail. When the wallet was created, the certificates for the most common CA’s (such as VeriSign, GTE, and Entrust) were included automatically. Contact your certifying authority if you need to add their certificate, and save the provided file as ca.crt in the wallet directory in a base64 format. Another option is to follow the instructions given below to create ca.crt from your server certificate (server.crt). If your Certifying Authority provided an intermediate certificate (to complete the chain) then save the provided file as intca.crt in a Base64 format, this will need to be imported into Oracle Wallet Manager prior to importing the server.crt. Certificates that comprise several parts (such as the P7B type) would also fall into this category
Creating your Certifying Authority’s Certificate
To create ca.crt
- Copy tech.crt to your PC (if necessary) using one of the following methods:
ftp (in binary mode) tech.crt to your pc copy the contents of server.crt and paste into notepad on the PC. Save the file as server.crt
- Double click on server.crt to open it with the Cyrpto Shell Extension.
- On the Certification Path tab click on the first (top) line and then View Certificate.
- On Details tab click Copy to File, this will start the export wizard.
- Click Next to continue.
- Select Base64 encoded X.509 (.CER) and click next.
- Click Browse and navigate to the directory of your choice.
- Enter ca.crt as the name and click ok to export the certificate.
- Close the wizard.
- Copy ca.crt back to your wallet directory (if necessary) using one of the following methods:
ftp (in binary mode) ca.crt to your application tier wallet directory copy the contents of ca.crt and paste into a new file in your application tier wallet directory using a text editor. Save the file as ca.crt
If there is intermediate cert,then export that also using same technique
Detailed steps to Import Certificate with screen shots
owm &
Then click wallet -> open
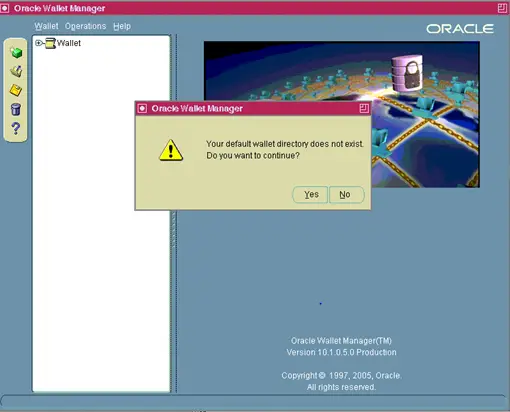
Click yes
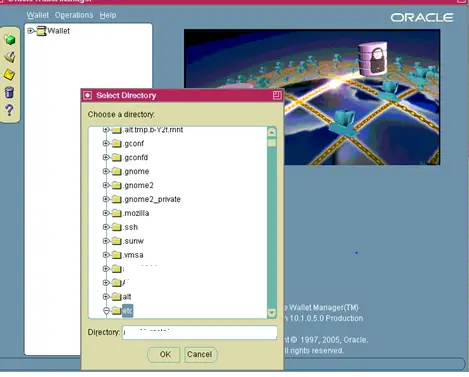
Enter the full path of the wallet directory
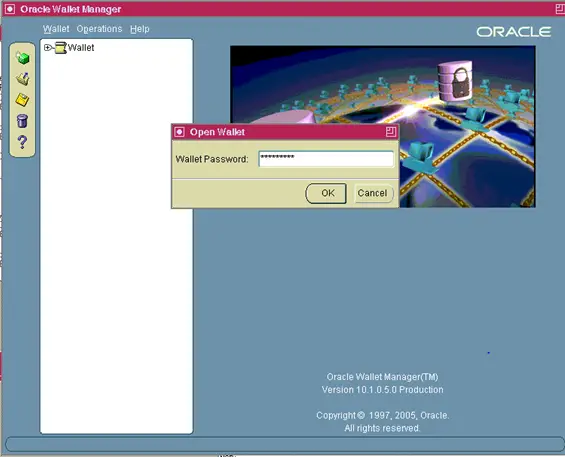
Enter the wallet password
Now Operations : Import User certficate
Alternatively you can add the certificate using orapki command also
orapki wallet add \
-wallet . \
-trusted_cert \
-cert ca.crt \
-pwd
orapki wallet add \
-wallet . \
-trusted_cert \
-cert int.crt \
-pwd
orapki wallet add \
-wallet .\
-user_cert \
-cert tech.crt \
-pwd
Important step
If you need to import the CA Certificate you will also need to add the contents of ca.crt file to b64InternetCertificate.txt file located in the 10.1.2 ORACLE_HOME/sysman/config directory:
$ cat ca.crt >> <10.1.2 ORACLE_HOME>/sysman/config/b64InternetCertificate.txt
If you were also provided an Intermediate Certificate (intca.crt) then you will also need to add that to the b64InternetCertificate.txt:
$ cat intca.crt >> <10.1.2 ORACLE_HOME>/sysman/config/b64InternetCertificate.txt
Step 6
Modify the OPMN wallet
- Navigate to the $INST_TOP/certs/opmn directory.
- Create a new directory named BAK.
- Move the ewallet.p12 and cwallet.sso files to the BAK directory just created.
- Copy the ewallet.p12 and cwallet.sso files from the $INST_TOP/certs/Apache directory to the $INST_TOP/certs/opmn directory.
Step 7
Update the JDK Cacerts File
Oracle Web Services requires the Certificate of the Certifying Authority who issued your server certificate (ca.crt from the previous step) to be present in the JDK cacerts file. In addition, some features of XML Publisher and BI Publisher require the server certficate (server.crt from previous step) to be present.
Follow these steps to be sure these requirements are met:
- Navigate to the $OA_JRE_TOP/lib/security directory.
- Backup the existing cacerts file.
- Copy your ca.crt and server.crt files to this directory and issue the following command to insure that cacerts has write permissions:
$ chmod u+w cacerts
Step 8
Update the Context File
Use the E-Business Suite – Oracle Applications Manager (OAM) Context Editor to change the SSL related variables as shown in this table:
| SSL Related Variables in the Context File | ||
| Variable | Non-SSL Value | SSL Value |
| s_url_protocol | http | https |
| s_local_url_protocol | http | https |
| s_webentryurlprotocol | http | https |
| s_active_webport | same as s_webport | same as s_webssl_port |
| s_webssl_port | not applicable | default is 4443 |
| s_https_listen_parameter | not applicable | same as s_webssl_port |
| s_login_page | url constructed with http protocol and s_webport | url constructed with https protocol and s_webssl_port |
| s_external_url | url constructed with http protocol and s_webport | url constructed with https protocol and s_webssl_port |
Step 9 – Run Autoconfig
Autoconfig can be run by using the adautocfg.sh script in the Application Tier $ADMIN_SCRIPTS_HOME directory.
Related Articles
Steps to Run Autoconfig On R12 Application including both Database and Application Tier
oracle apps autoconfig templates location and How to customize the template for autoconfig files
Step 10 – Restart the Application Tier services
Use the adapcctl.sh script in the $ADMIN_SCRIPTS_HOME directory to stop and restart the Application Tier Apache services.
Steps to be used when going for SSL terminator with Oracle apps R12
There is no need for certificate creation and installation on the web server.Certificate will be installed in SSL terminator. In this case, we just need to set the context file parameter given below
| Changes when using an SSL Accelerator | ||
| Variable | Non-SSL Value | SSL Value |
| s_url_protocol | http | http |
| s_local_url_protocol | http | http |
| s_webentryurlprotocol | http | https |
| s_active_webport | same as s_webport | value of the SSL Accelerator’s external interfacing port |
| s_webentryhost | same as s_webhost | SSL Accelerator hostname |
| s_webentrydomain | same as s_domainname | SSL Accelerator domain name |
| s_enable_sslterminator | # | remove the ‘#’ to use ssl_terminator.conf in ssl terminated environments |
| s_login_page | url constructed with http protocol and s_webport | url constructed with https protocol, s_webentryhost, s_webentrydomain, s_active_webport |
| s_external_url | url constructed with http protocol and s_webport | url constructed with https protocol, s_webentryhost, s_webentrydomain, s_active_webport |
Run Autoconfig
Autoconfig can be run by using the adautocfg.sh script in the Application Tier $ADMIN_SCRIPTS_HOME directory.
Restart the Application Tier services
Use the adapcctl.sh script in the $ADMIN_SCRIPTS_HOME directory to stop and restart the Application Tier Apache services.
Steps for End to end encryption with Pass through configuration on Load Balancer
1) All the steps given for single web server need to be executed.
2) The certificate need to be created with load balancer Name
3) We can execute the certificate steps on one Node and then copy all the steps to the other nodes
Context value changes
| SSL Related Variables in the Context File | ||
| Variable | Non-SSL Value | SSL Value |
| s_url_protocol | http | https |
| s_local_url_protocol | http | https |
| s_webentryurlprotocol | http | https |
| s_active_webport | same as s_webport | same as s_webssl_port |
| s_webssl_port | not applicable | default is 4443 |
| s_https_listen_parameter | not applicable | same as s_webssl_port |
| s_login_page | url constructed with http protocol and s_webport | url constructed with https protocol and s_webssl_port |
| s_external_url | url constructed with http protocol and s_webport | url constructed with https protocol and s_webssl_port |
Run Autoconfig
Autoconfig can be run by using the adautocfg.sh script in the Application Tier $ADMIN_SCRIPTS_HOME directory.
Restart the Application Tier services
Use the adapcctl.sh script in the $ADMIN_SCRIPTS_HOME directory to stop and restart the Application Tier Apache services.
Database setup required
Oracle products such as Oracle Configurator, Order Management, iStore, Order Capture, Quoting, iPayment, iStore, and Pricing access data over the Internet in HTTP or HTTPS connection mode. The implementation of SSL for the Oracle Database Server (which acts as a client sending requests to the Web server) makes use of the Oracle Wallet Manager for setting up an Oracle wallet.
Note: This is a mandatory requirement for Oracle iStore storefront pages when the Web Tier is also SSL enabled.
To enable HTTPS Client request from the Database via UTL_HTTP you need to establish a truststore in wallet format. You do not need a server certificate for this wallet. You only need to import the root CA certificate for the root CAs that are the trust anchor for the the sites you need UTL_HTTP to connect to.
2)Create a new wallet directory named: wallet
3)Navigate to the newly created wallet directory.
4) Open the Wallet Manager as a background process:
owm &
5)On the Oracle Wallet Manager Menu navigate to Wallet -> New.
Answer NO to: Your default wallet directory doesn’t exist. Do you wish to create it now?
The new wallet screen will now prompt you to enter a password for your wallet.
Click NO when prompted:
A new empty wallet has been created. Do you wish to create a certificate request at this time?6) If you need to import ca.crt:
On the Oracle Wallet Manager menu navigate to Operations -> Import Trusted Certificate.
Click OK.
Double click on ca.crt to import it.7) Save the wallet:
On the Oracle Wallet Manager Menu click Wallet.
Verify the Auto Login box is checked.
Click Save.
To test that the wallet is properly set up and accessible, login to SQLPLUS as the apps user and execute the following:SQL>select utl_http.request(‘[address to access]’, ‘[proxy address]’, ‘file:[full path to wallet directory]’, null) from dual;
where:
‘[address to access]’ = the url for your E-Business Suite Rapid Install Portal.
‘[proxy address]’ = the url of your proxy server, or NULL if not using a proxy server.
‘file:[full path to wallet directory]’ = the location of your wallet directory (do not specify the actual wallet files).
The final parameter is the wallet password, which is set to null by default.
Related links
Enabling SSL or TLS in Oracle E-Business Suite Release 12 (Doc ID 2143099.1)
How to find R12 components Version
40 Adpatch question every DBA should know
awk command
Keytool command
Thanks and very informative, great Job.